The Rise of Preemptive Cyber Defense: A Must-Have Strategy for Security Leaders
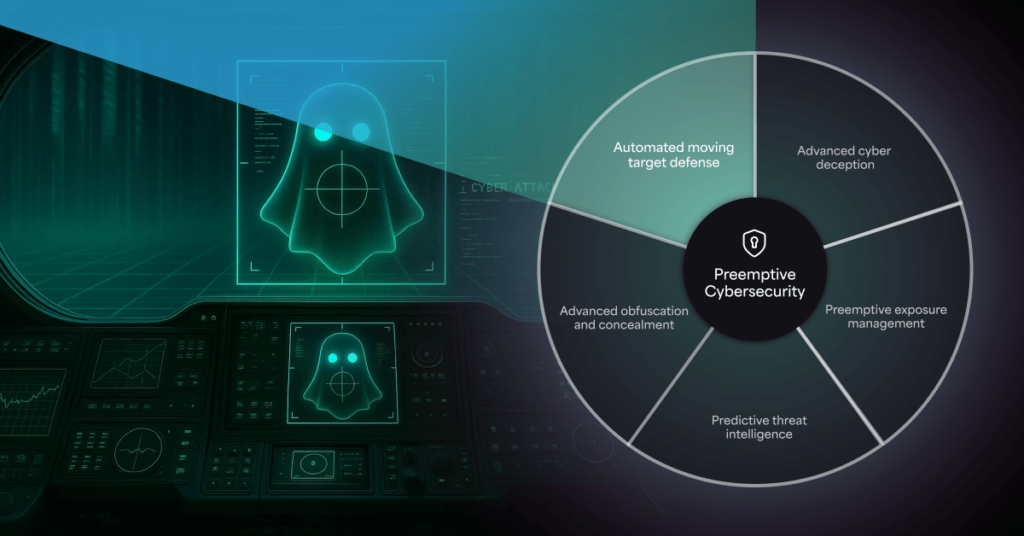
As cyber threats continue to evolve in complexity, traditional and reactive approaches like detection and response are no longer enough. Security leaders now face a new frontier: preemptive cyber defense. This emerging approach prioritizes stopping threats before they materialize, leveraging technologies like Automated Moving Target Defense (AMTD) to fortify organizational defenses against novel and sophisticated cyberattacks.
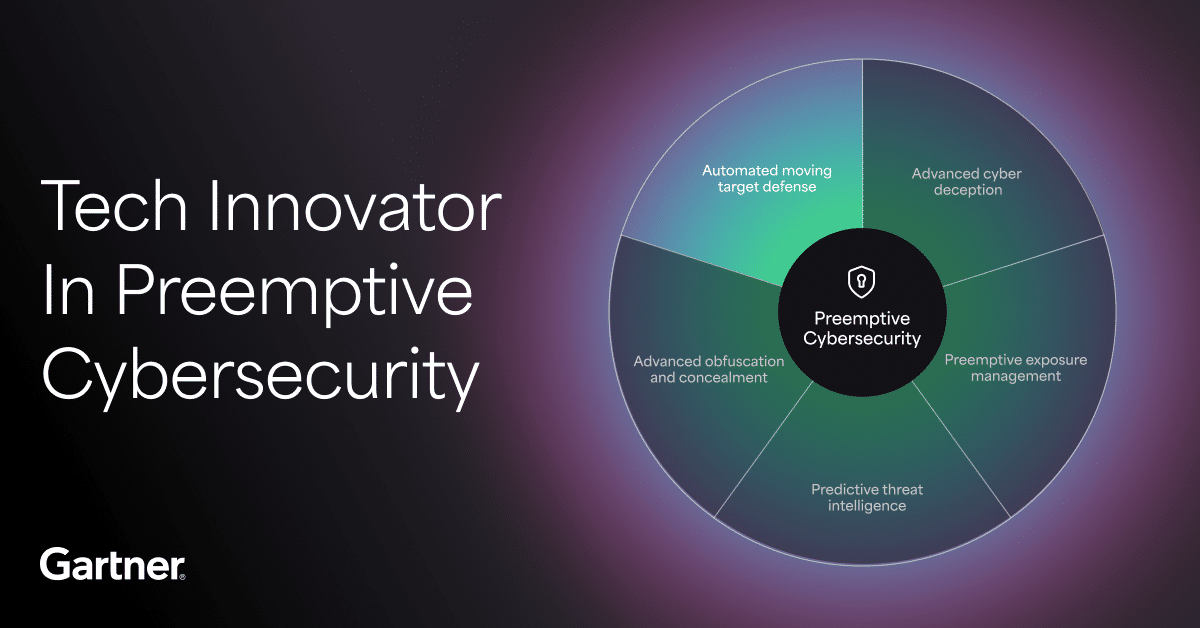
While still in its early stages, the adoption of preemptive cyber defense is expected to outpace the adoption rate of detection and response-based technologies like Endpoint Detection and Response (EDR). According to Gartner, “By 2030, preemptive cybersecurity technologies will be included in 75% of security solutions that are currently focused solely on detection and response.”1
Here’s why it’s time for organizations to embrace this innovative strategy and technology like AMTD.
1. Combating AI-Supported Attack Techniques
The rise of AI-powered cyberattacks has amplified the need for proactive security measures. Malicious actors now use AI to bypass traditional defenses, conduct reconnaissance, and launch highly adaptive attacks. Preemptive cyber defense technologies counter this by leveraging AI for predictive analytics, real-time threat modeling, and automated prevention strategies.
As highlighted in the Gartner Emerging Tech: Top Challenges in Preemptive Cyber Defense Report, preemptive cyber defense solutions are designed to continuously identify, prioritize, and mitigate vulnerabilities before they are exploited. This includes capabilities like morphing attack surfaces, deploying deception technologies, and executing AI-driven playbooks to neutralize threats in their earliest stages.
2. Beyond Detection and Response: Filling the Gaps
While detection and response technologies remain critical in the cybersecurity stack, they are inherently reactive. Attackers exploit this delay, often deploying advanced tactics like in-memory attacks, ransomware, and fileless malware that can evade traditional and signature-based defenses.
Preemptive cyber defense addresses these gaps by shifting the focus to prevention.
For example, AMTD technology dynamically changes attack surfaces, making it nearly impossible for threat actors to locate and exploit vulnerabilities. This proactive approach reduces reliance on post-incident remediation and stops attacks before they can do damage.
Another added benefit: integrating preemptive cyber defense with existing detection and response tools enhances their efficacy. By reducing false positives security teams can allocate more resources to high-impact incidents. This creates a more efficient and effective cybersecurity ecosystem.
3. The Power of AMTD
Attackers continuously adapt their techniques to counter the predictability that detection and response solutions rely on. Conversely, organizations must embrace adaptability to ensure a robust cybersecurity posture.
Morphisec’s pioneering AMTD technology is designed to enhance an organization’s defense by continuously and automatically changing the attack surface. Unlike traditional static defenses that maintain fixed system configurations and are predictable over time, AMTD introduces dynamic variability into the environment, like shifting IP addresses, altering network paths, or frequently changing system configurations.
The core idea behind AMTD is to create uncertainty for attackers. By frequently altering key system attributes, it disrupts the reconnaissance and attack planning phases, making it difficult for adversaries to locate and exploit weaknesses.
By integrating preemptive cyber defense capabilities like AMTD into their security stack, organizations can achieve several benefits:
- Proactive Threat Prevention: By identifying and addressing vulnerabilities before they are exploited, organizations can stop attacks before they begin.
- Minimized Attack Surface: Continuous monitoring and dynamic security controls reduce potential attack vectors, limiting opportunities for threat actors.
- Increased Resilience: A protection-focused strategy ensures organizations can swiftly adapt to evolving threats, maintaining operational stability even against advanced cyberattacks.
- Operational Efficiency: Automated defenses and prioritized risk management streamline workflows, enabling security teams to focus on high-priority threats with greater effectiveness.
This constant change forces attackers to spend more time and resources identifying their targets, increasing the chances of detection or failure before they can launch a successful attack. AMTD is particularly effective in combating sophisticated threats, like in-memory attacks, zero-day attacks, advanced persistent threats (APTs) and ransomware.
4. Overcoming Adoption Barriers
Despite its advantages, many organizations hesitate to adopt preemptive cyber defense strategies. Common concerns include perceived costs, complexity, and the need to maximize existing tech investments. However, these challenges are often based on misconceptions.
Technologies like AMTD are designed to complement rather than replace existing security solutions. They integrate seamlessly with current infrastructure, enhancing its value by reducing alert fatigue. In fact, AMTD often requires minimal additional overhead, as its proactive and preventative processes reduce manual intervention and resource strain.
The Path Forward is Preemptive Cyber Defense
Preemptive cyber defense represents the next evolution in cybersecurity, addressing the limitations of traditional methods while tackling the sophisticated threats of tomorrow. By embracing this approach, security leaders can shift from a reactive to a proactive stance, fortifying their organizations against the ever-changing cyber landscape.
Now is the time to invest in preemptive cyber defense. Not only does it offer enhanced protection, but it also maximizes the value of an organization’s current security investments, paving the way for a more resilient and future-proof cybersecurity strategy.
Learn more about preemptive cyber defense and see Morphisec AMTD in action — book a personalized demo today.
1Gartner, Emerging Tech: Tech Innovators in Preemptive Cybersecurity, Luis Castillo, Isy Bangurah, 8 January 2025
2Gartner, Emerging Tech: Top Challenges in Preemptive Cyber Defense, Lawrence Pingree, Isy Bangurah, Luis Catillo, Walker Black. 22 October 2024
GARTNER is a registered trademark and service mark and Hype Cycle is a registered trademark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.