Decoding the Puzzle: Cicada3301 Ransomware Threat Analysis
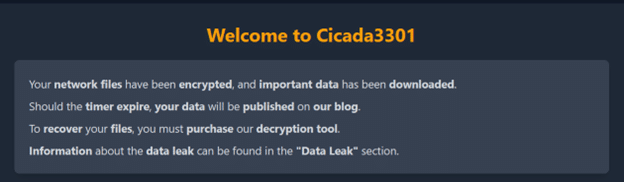
In the rapidly evolving landscape of cybersecurity threats, a new adversary has emerged, drawing inspiration from one of the internet’s most enigmatic puzzles—Cicada3301. This new threat, dubbed Cicada3301 ransomware, was identified in a Morphisec customer environment just a week ago after bypassing a leading endpoint and detection and response (EDR) provider solution.
Introduction
Cicada3301 ransomware, written in Rust, was first reported less than two months ago. Despite its recent emergence, Morphisec threat researchers have already identified striking similarities between Cicada3301 and the infamous BlackCat ransomware.
Like its namesake, the Cicada puzzle, which has long been associated with complex, cyber-related problem-solving, the true identity of the Cicada3301 ransomware developers remains shrouded in mystery.
However, it’s crucial to note that Morphisec’s anti-ransomware impact protection has already proven effective against Cicada3301 without requiring any updates, highlighting Morphisec’s robustness and adaptability in the face of emerging threats.
During Morphisec’s investigation, additional tools were uncovered, such as EDRSandBlast, which is used to tamper with EDR systems. With the limited visibility Morphisec researchers currently have, it appears that Cicada3301 ransomware primarily targets small to medium-sized businesses (SMBs), likely through opportunistic attacks that exploit vulnerabilities as the initial access vector.
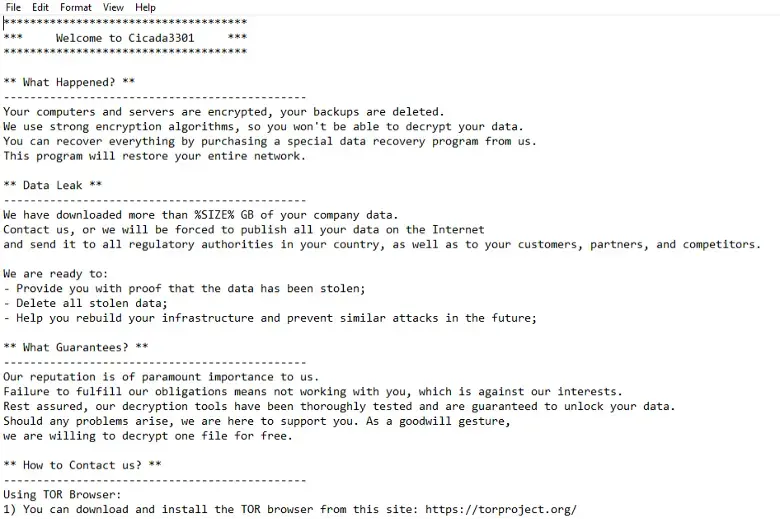
Since June 18, 2024, Morphisec has counted more than 20 victims, predominately located in North America and England. Impacted organizations vary in size, from SMB (13 organizations) and mid-sized businesses (5 organizations) to enterprise (3). Industries of operation include manufacturing/industrial, healthcare, retail and hospitality. Attackers accept payment in Bitcoin and Monero.
Technical Details
Cicada3301 ransomware shares several core characteristics with the well-known Rust-based ransomware, BlackCat.
It features a well-defined parameter configuration interface, registers a vector exception handler, and employs similar methods for shadow copy deletion and tampering. This trend of using Rust in ransomware development is on the rise, with other notable examples including Hive and RansomExx, due to Rust’s efficiency and cross-platform capabilities.
However, Cicada3301 distinguishes itself with significant innovations, particularly in how it executes and integrates compromised credentials, marking an evolution in ransomware tactics.
Download Morphisec’s full Cicada3301 analysis including Indicators of Compromise (IOCs)
How Morphisec Helps
Powered by Automated Moving Target Defense (AMTD), Morphisec’s Anti-Ransomware Assurance Suite stops ransomware attacks like Cicada3301 with multi-layered protection.
Ransomware infiltration protection prevents the execution of ransomware attacks at early infiltration stages with Morphisec’s prevention-first AMTD technology that constantly changes a system’s configuration or environment. This makes it harder for attackers to exploit systems as the attack surface is always shifting.
Ransomware impact protection defends systems against the ransomware impact phase with dedicated anti-ransomware protection that proactively defends critical assets and files with a prevention-first strategy. This minimizes recovery times and strengthens an organization’s anti-ransomware stance.
Preventatively, Adaptive Exposure Management (AEM) helps teams adapt by pre-emptively defending against attacks. AEM prioritizes vulnerabilities, automates the assessment and validation of an organization’s security controls, identifies high-risk software and addresses security misconfigurations.
Morphisec doesn’t rely on signature or behavioral patterns. Instead, its patented AMTD technology prevents an attack at its earliest stages, preemptively blocking attacks on memory and applications, and effectively remediating the need for response.
Schedule a demo today to see how Morphisec stops ransomware and other new and emerging threats.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.