Tech Evaluation: Automated Moving Target Defense Research Guide

When it comes to the cybersecurity tech stack, many teams admittedly suffer from tech bloat. In many ways the continuous evolution of the threat landscape and an ever-growing list of unique use cases has made tech bloat inevitable. Tools consolidation is a trending theory, but in application, deciding which technologies to remove can feel like a dangerous game of Jenga.
Understanding your organization’s attack surface, its unique use cases and security maturity are integral in determining which technologies are critical versus optional — or redundant.
Currently industry watchers like IT-Harvest and Richard Steinnon are tracking 17 major technology categories, more than 1,000 subcategories and an eye-watering 8,000 products — as a security buyer you’re spoiled for choice. But as you and your team have likely experienced, unique technologies can be great for solving unique use cases, but useless if they don’t complement your larger defense-in-depth strategy and core toolsets.
Shifting the focus from Detection and Response to Prevention
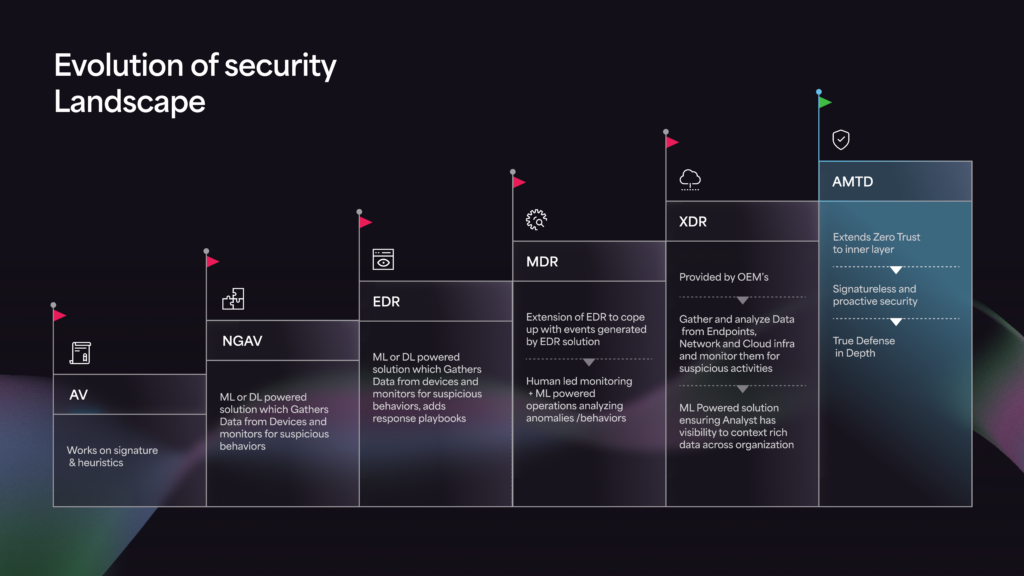
The evolution of cybersecurity started with anti-virus (AV) software, which primarily performed static analysis of binaries and files to identify known malware. Next-generation anti-virus (NGAV) software and endpoint protection platforms advanced this approach by adding dynamic analysis, which involves executing a file in a sandboxed environment to observe its behavior.
Endpoint detection and response (EDR), extended detection and response (XDR), and managed detection and response (MDR) technologies took this further by incorporating behavioral analysis. EDR technology monitors execution on a computer, hooks into critical functions and syscalls to understand behavior in real time and analyzes not just the binary but the entire execution context.
Automated Moving Target Defense (AMTD) represents the future of cybersecurity. Unlike previous technologies that focus on detection and response, AMTD is preventive. Inspired by a basic military strategy—where a moving target is harder to attack than a stationary one—AMTD orchestrates movements or changes within IT environments across the attack surface. This increases uncertainty and complexity for attackers, making it significantly more challenging for them to succeed.
AMTD empowers organizations, helping them shift from a position of “detect and respond”, to “preemptive defense” by fundamentally changing the security paradigm. This game-changing technology effectively and efficiently prevents attacks before they can gain traction; instead of waiting for an attack to occur, AMTD instead proactively hinders it by continuously changing a system’s configuration.
Morphisec AMTD uses an ultra-lightweight agent to block unauthorized processes deterministically, as opposed to probabilistically. It generates fewer false positive alerts and doesn’t noticeably affect system performance. With Morphisec AMTD and its seamless integration security leaders can augment and complement installed NGAV, EPP, EDR, and XDR with defense-in-depth that stops evasive and undetectable attacks.
Learn more about AMTD in our Adaptive Cyber Resiliency White Paper
Vetting AMTD Technology and Solutions
Not all AMTD technology is equal — capabilities and functionality can vary. For example, while most solutions feature polymorphism as a key feature, many don’t offer expanded and critical functionality like Adaptive Exposure Management, virtual patching and anti-ransomware assurance. Deployment, integration and resource intensity are additional factors to consider when evaluating AMTD technology.
Gartner covers AMTD extensively; the following reference guide lists key AMTD research and insights that can help security leaders and their teams understand core capabilities, components and selection criteria. Gartner subscribers can access all research through the Gartner portal.
| Hype Cycle Research | Publish Date |
|---|---|
| Hype Cycle for Endpoint Security, 2024 (complimentary access courtesy of Morphisec) | August 8, 2024 |
| Hype Cycle for Endpoint Security, 2023 | August 1, 2023 |
| Additional Research | Publish Date |
|---|---|
| How to Protect Your Clouds with CSPM, CWPP, CNAPP and CASB | October 2, 2024 |
| Top Strategic Technology Trends for 2024: Continuous Threat Exposure Management | October 16, 2023 |
| Securing End-of-Support Production Systems | March 15, 2023 |
Making a business case for new technology spend
As you vet solutions and lobby for new technology like AMTD, making a business case for technology spend can be a significant hurdle. Annual Loss Expectancy (ALE), also known as Annualized Loss Expectancy is a popular tool used in risk assessments, and it’s gaining traction and importance in cybersecurity investment decision-making processes.
ALE estimates the potential financial impact of security investments over a specific period. It helps identify and prioritize security threats by assigning a monetary value to the anticipated annual costs of specific security breaches. This, in turn, supports the development of a strong business case for targeted technological investments, particularly when there might be an overlap or redundancy in existing technologies.
A refined ALE calculation considers a business’s risk tolerance and profile, quantifying potential risks in the event of a breach. This includes evaluating the costs of various risk scenarios and their likelihood of occurring within a given period, considering the effectiveness of current security measures.
The resulting ALE value:
- Establishes a benchmark to determine whether the costs of the organization’s controls are in line with or below the ALE baseline.
- Projects annual potential losses, providing insights into the value of security investments and helping business stakeholders support risk mitigation strategies.
Calculating ALE involves combining the monetary costs of individual security incidents, such as a ransomware attack, with the expected annual probability of their occurrence. This comprehensive approach helps business leaders (confidently) make well-informed decisions regarding cybersecurity investments, while security leaders can ensure resilience against potential threats.
How Morphisec can help
Morphisec’s Anti-Ransomware Assurance Suite (powered by Morphisec’s pioneering AMTD technology) helps organizations improve their overall security posture and strengthen defense-in-depth strategy.
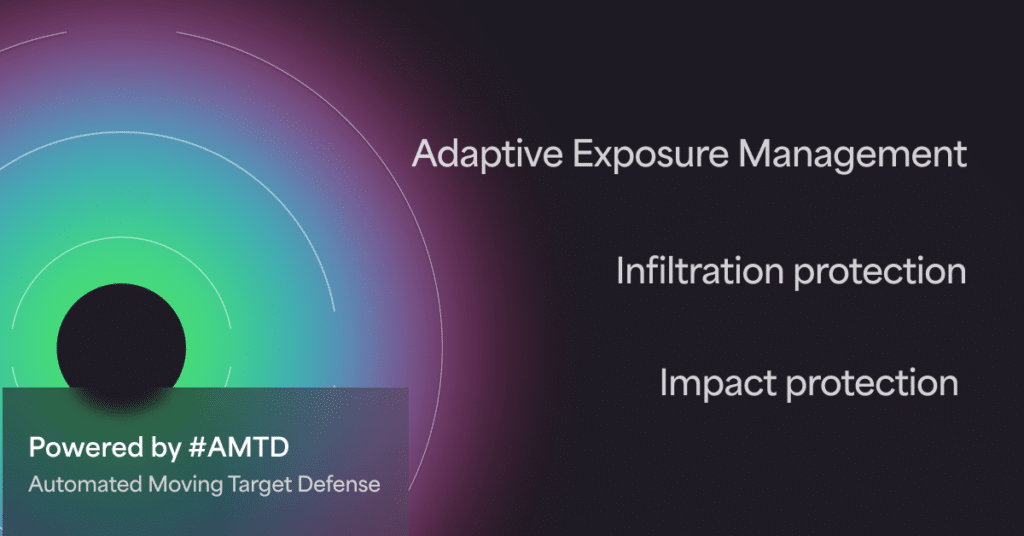
Anti-Ransomware Assurance Suite modules include:
- Adaptive Exposure Management — Helping organizations adapt by elevating the overall security posture and pre-emptively defending against attacks. Adaptive Exposure Management prioritizes vulnerabilities, automates the assessment and validation of an organization’s security controls, identifies high-risk software, and addresses security misconfigurations.
- Infiltration Protection — Preventing the execution of ransomware attacks at early infiltration stages with Morphisec’s prevention-first AMTD technology that constantly changes a system’s configuration or environment. This makes it harder for attackers to exploit vulnerabilities as the attack surface is always shifting.
- Impact Protection — Defending systems against the ransomware impact phase with dedicated anti-ransomware protection that proactively defends critical assets and files with a prevention-first strategy. This minimizes recovery times and strengthens an organization’s anti-ransomware stance.
With the Anti-Ransomware Assurance Suite and Morphisec’s industry-leading AMTD technology, security leaders get a clear understanding of their attack surface, identify the unique factors that affect it, and gain the ability to address those factors before impact, all while enhancing the functionality and value derived from their other security investments.
See Morphisec AMTD in action — schedule a demo today.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.





















