Automated Moving Target Defense
Next generation, automated cybersecurity for stopping ransomware, supply chain attacks, zero-days, fileless and other undetectable attacks in-memory at runtime. Ideal for augmenting NGAV, EDR and XDR with no additional staff needed and no performance impact on endpoints or servers.
What is it?
What is Automated Moving Target Defense?
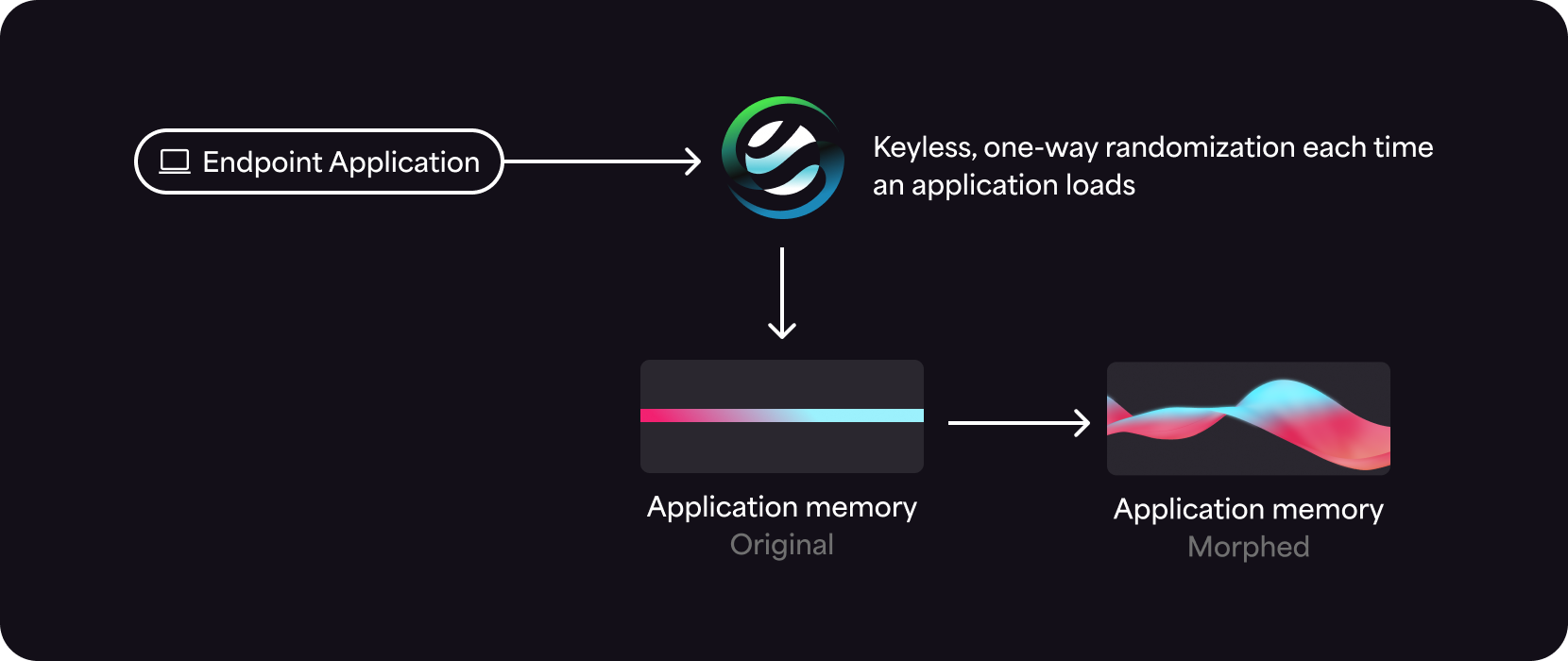
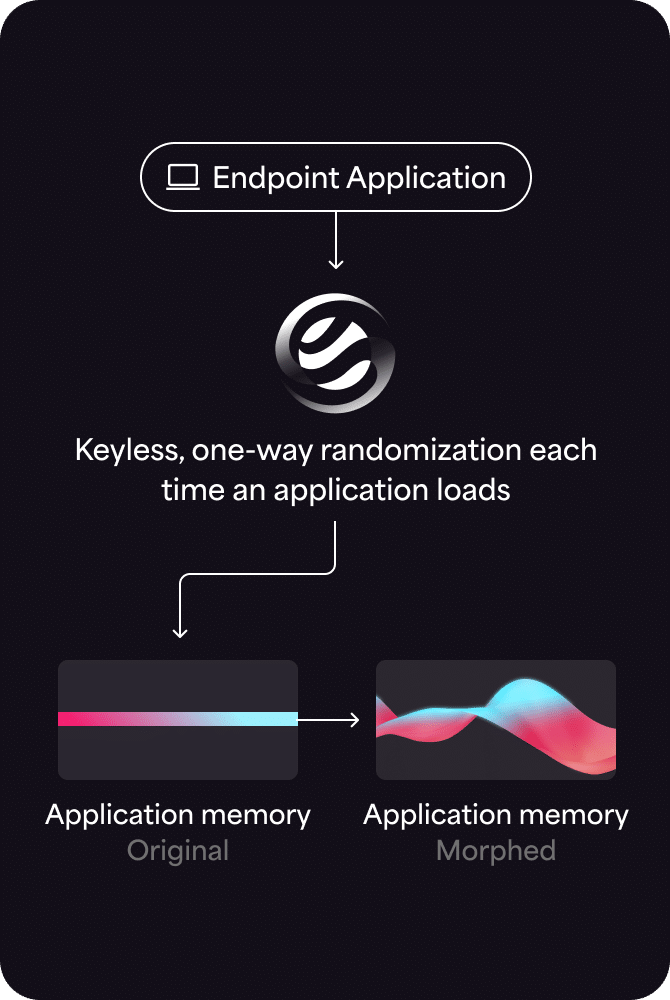
Automated Moving Target Defense (AMTD) is a proactive cyber defense strategy that protects systems by making them unpredictable and difficult to attack. AMTD works by changing and moving system resources, such as runtime memory, to create a constantly shifting attack surface. This makes it harder for attackers to find and exploit vulnerabilities.
AMTD, also called Moving Target Defense (MTD), prevents ransomware, supply chain attacks, zero-day attacks, fileless attacks, in-memory attacks, and other advanced threats. It uses system polymorphism in memory to hide operating system and application targets from adversaries in an unpredictable manner. This leads to a dramatically reduced attack surface and lower security operating costs.

How it works
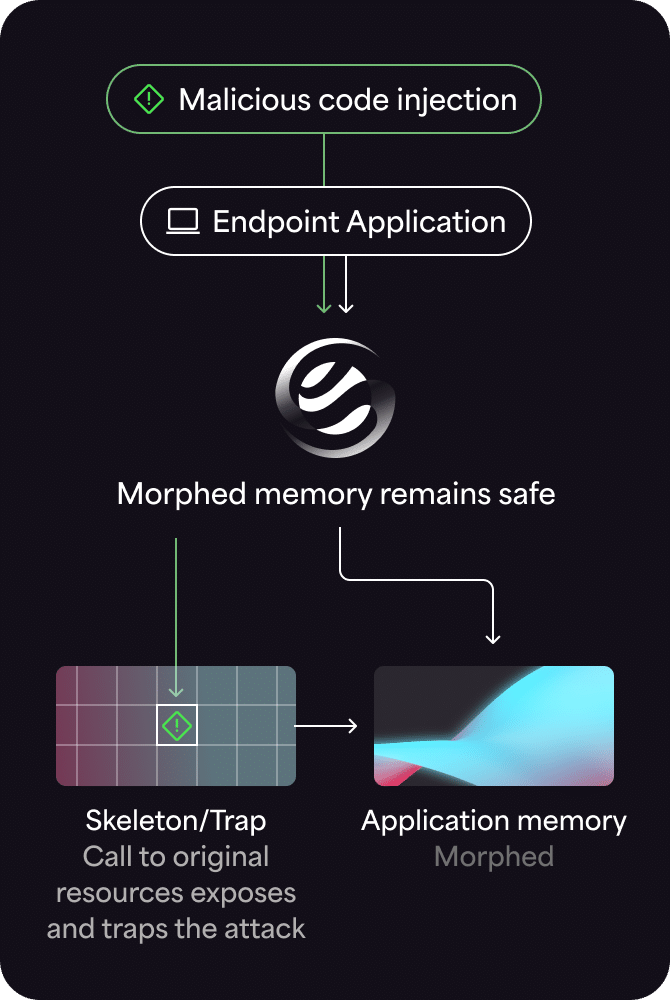
Moving Target Defense explained
Despite massively expanding investment in cybersecurity, damage from cyberattacks continues to rise at an unprecedented rate, projected to reach over $10 trillion by next year. If existing solutions were working, ransomware and supply chain breaches wouldn’t be happening and inflicting so much financial devastation, brand erosion, and business loss. Today’s solutions are manifestly not countering threat actors’ advanced attacks.
Next generation antivirus (NGAV), endpoint protection platforms (EPP), and endpoint detection and response (EDR and XDR) solutions stop known attacks with recognized signatures and behavioral patterns. But they often do not detect or prevent the more disruptive advanced attacks organizations are experiencing today – the undetectable attacks such as zero-days, malware variants or supply chain attacks that lead to ransomware. A new technology recognized by Gartner is proven to stop advanced threats pre-emptively, making prevention-first security a reality: Moving Target Defense (MTD), also known as Automated Moving Target Defense (AMTD).
Automated Moving Target Defense research guide
Your one-stop-shop for Gartner research to help select Automated Moving Target Defense technology and solutions.

Benefits
What are the benefits of Moving Target Defense?
The mainstream paradigm of cybersecurity has long focused on detection and response. This approach is inherently reactive, and cedes the innovation advantage to threat actors.
AMTD changes the calculus of protecting critical systems. It is a proactive, prevention-first system. It interrupts the progression of cyberattacks and stops threat actors’ ability to gain persistence in target organizations.
“The US Department of Homeland Security defines Moving Target Defense as, “controlled change across multiple network and system dimensions to increase uncertainty and complexity for attackers by reducing their window of opportunity and increasing the costs of their probing and attack efforts.”

Automated Moving Target Defense lowers IT and security team costs and effort by slashing ‘false positive’ security alerts, IT support tickets, and analyst alert triage time.
It protects critical systems through the same kind of polymorphism and evasion that adversaries have used to great effect in the past 10 years. It provides a proactive approach for defenders, rather than waiting for threat actors to breach their systems and find the holes. It empowers organizations to prevent breaches on the endpoint before they can spread and perpetrate ransomware.
Use cases
Why is Moving Target Defense needed?
Almost all malicious software, or malware, was once executable files on disc or the operating system (OS). These executables leave behind evidence of their existence. Tools like antivirus (AV), NGAV, EPP, EDR, and XDR evolved to spot telltale signs of malware deployment, such as attack patterns and signatures. They would then isolate threats before they could do real damage.
But sophisticated threat actors are wise to traditional cybersecurity tools. Attack chains increasingly hijack legitimate system processes for malicious ends or target device memory at runtime rather than the disc or OS. Hijacked legitimate system processes and in-memory threats offer little, if anything, in the way of signatures to detect or behavior patterns to analyze.
Legitimate system processes must work in memory at runtime, but this environment is mostly invisible to current cybersecurity tools. To catch an attack in progress, they need to scan device memory multiple times while an application is running and listen to the correct triggering operations to find malicious patterns. But in a typical application’s runtime environment, there might be 4GB of virtual memory. Even when dialed to the most aggressive alert settings, it’s impossible to scan this volume of data often enough. At least without slowing down an application so much as to make it barely usable.
To ensure usability, memory scanners can only look for highly specific parameters, at specific memory locations, and at specific timeline triggers. In a best-case scenario, a scanning-focused solution might scan a small fraction of application memory. But threats also now use polymorphism to obfuscate their presence, so catching malicious activity in such a small sample of device memory would be miraculous.
Aggressive alert settings also result in a vast number of false positive alerts that require extra resources to analyze. If a high number of alerts and false positives aren’t an issue for an organization using current cybersecurity tools, their alert setting is probably too low. They are almost certainly missing the most disruptive advanced attacks.
This is why organizations need MTD.
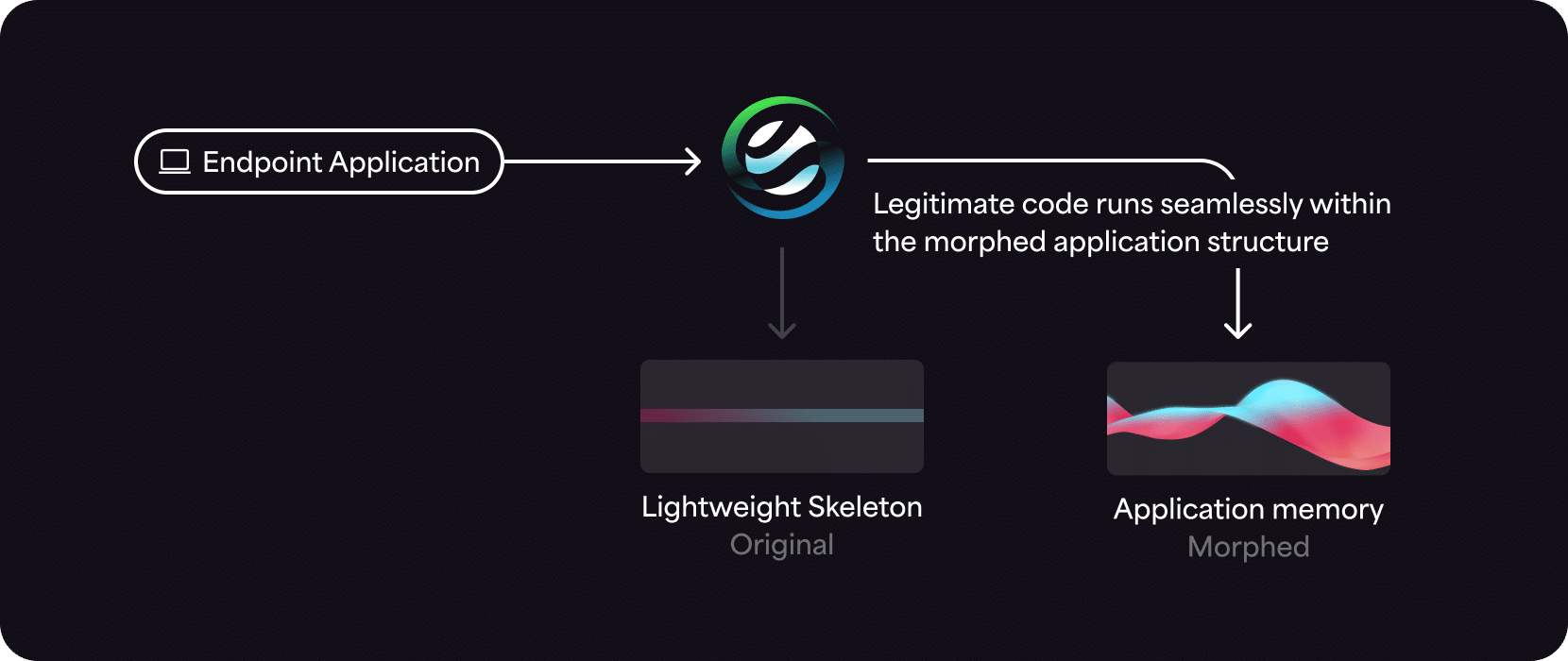
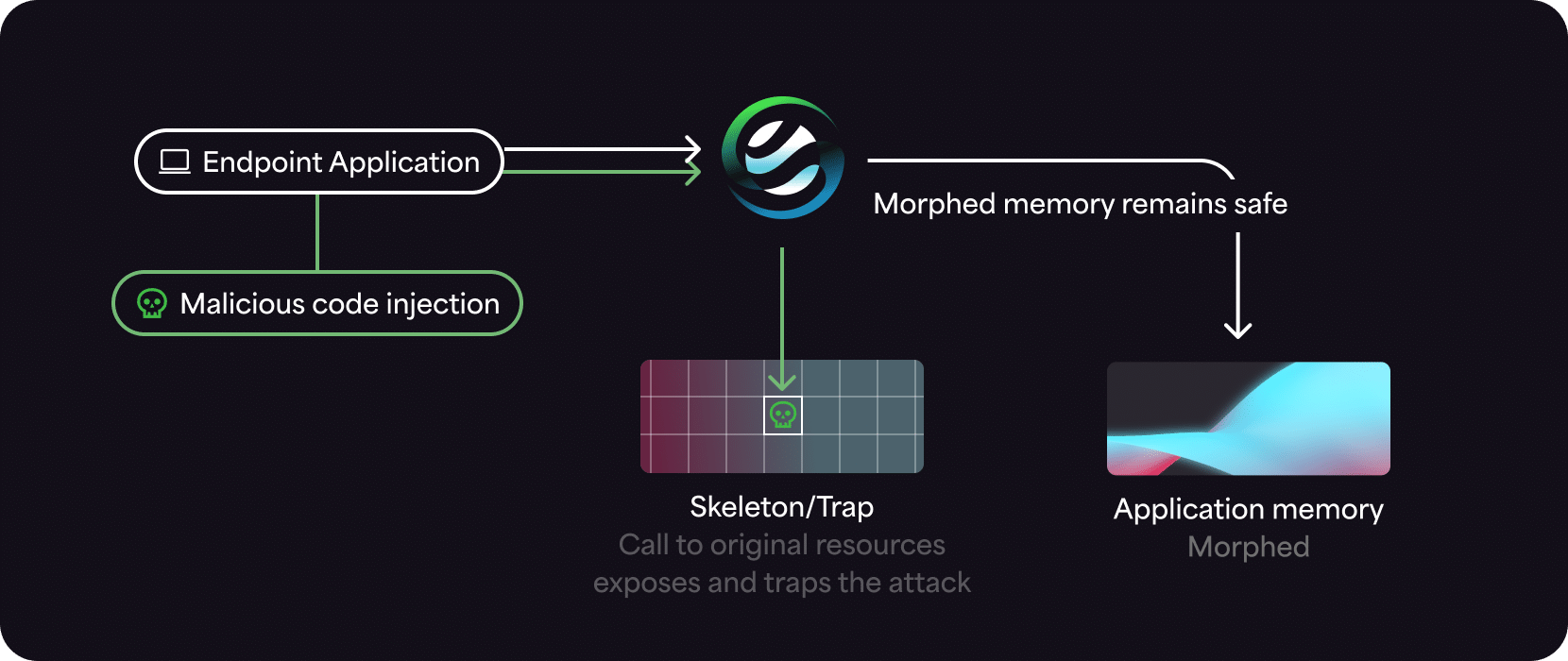
Automated Moving Target Defense technology morphs the runtime memory environment to create a continually changing, unpredictable attack surface. This means that even in the highly unlikely event a threat actor can find their target once, they’re unable to reuse that attack on another device or even later on in the same device. MTD uses an ultra-lightweight agent to block unauthorized processes deterministically, as opposed to probabilistically. This means MTD generates a few false positive alerts and doesn’t noticeably affect system performance. It integrates seamlessly into a tech stack to augment NGAV, EPP, EDR, and XDR with Defense-in-Depth to stop in-memory, fileless, zero-day, supply chain attacks, and other advanced threats.
Summary
Moving Target Defense: innovative and disruptive technology
Moving Target Defense uses techniques similar to those of attackers, such as polymorphism, deception, and evasion. It obfuscates targets by randomizing application memory runtime so a threat actor can’t accurately identify their target.
Imagine a fork in a road with a road sign. In one direction is a mansion full of riches. In the other direction is a dangerous, sheer cliff. MTD switches which way the road sign points.
Threat actors who travel this imaginary road are diverted to the sheer cliff. Meanwhile, legitimate traffic is still sent to the mansion. Employees get work done, while threat actors are refused entry. AMTD, also called Moving Target Defense (MTD), prevents ransomware, supply chain attacks, zero-day attacks, fileless attacks, in-memory attacks, and other advanced threats. It uses system polymorphism in memory to hide operating system and application targets from adversaries in an unpredictable manner. This leads to a dramatically reduced attack surface and lower security operating costs.
FAQs
What is Moving Target Defense?
Moving Target Defense (MTD) is a preemptive cybersecurity strategy that employs system polymorphism to make operating systems and applications unpredictable. By continuously altering the attack surface, MTD complicates efforts by attackers to locate and exploit vulnerabilities, significantly enhancing overall security.
What is the difference between MTD and AMTD?
Moving Target Defense (MTD) is a general strategy that involves changing and moving system resources to create an unpredictable attack surface. Automated Moving Target Defense (AMTD) enhances this by automating these changes, making the system continuously dynamic without manual intervention, thereby increasing the complexity for attackers.
What is the difference between AMTD and ASLR?
Windows ASLR works at system boot-time, then the system is static. ASLR’s mechanisms are known by attackers and can be bypassed using memory read iterations and other exploits. ASLR doesn’t include traps, so while protecting memory, malicious processes continue to run, and there is no attack visibility.
AMTD works at process load time, creating a continually changing attack surface. It also creates decoy traps, which provides visibility into malicious processes and triggers their termination.
What is the Moving Target Defense approach?
The Moving Target Defense approach involves continuously altering system configurations and environments. By doing so, it increases uncertainty and complexity for attackers, reducing their chances of finding and exploiting vulnerabilities. This preemptive method disrupts attack patterns by providing no consistent target.
What are the different types of Moving Target Defense?
Environment and Artifact Deception: Uses deceptive tactics such as bait data and simulated environments to mislead and trap attackers, making cyber attacks self-defeating by exposing the attackers.
Dynamic Network Defense: Utilizes technologies that alter network configurations and traffic routes dynamically, increasing unpredictability to prevent interception or manipulation by attackers.
Memory Attack Prevention: Protects servers and workstations by continuously changing memory handling techniques to block exploits.
Storage Defense: Applies changing strategies in data storage and retrieval within storage networks to thwart data corruption or unauthorized access.
Deception Across Contexts: Deploys a variety of misleading signals and information across multiple IT layers, confusing attackers and diluting their efforts.
Keep reading about AMTD
See Automated Moving Target Defense in action
Schedule a personalized demo to see how AMTD prevents ransomware, zero-day, fileless, and other advanced attacks that other technologies don’t.